Security logs
in this section you can monitor access to the system including failed attempts and their reason.
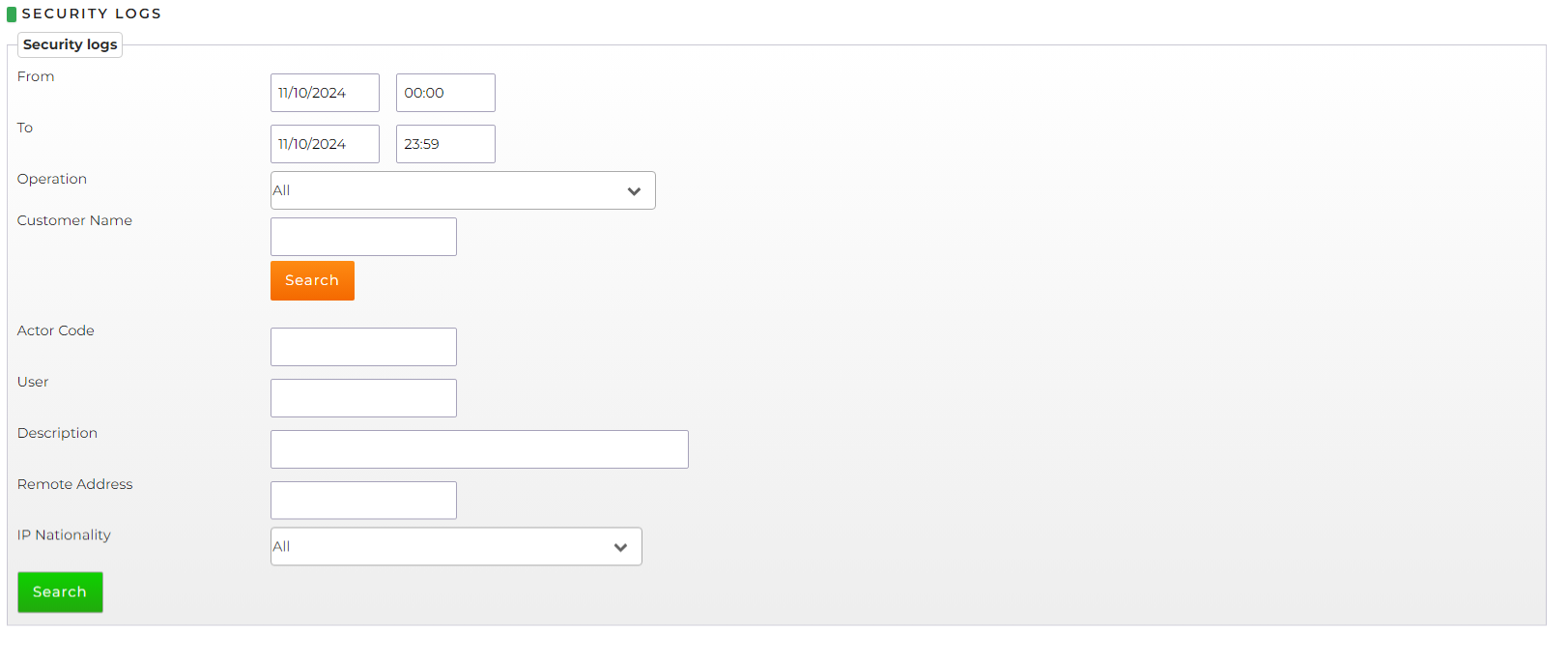
- From/To: you can define start and end dates and times
-
Operation you can filter by choosing between:
- All
- API - Unauthorized IP in booking request
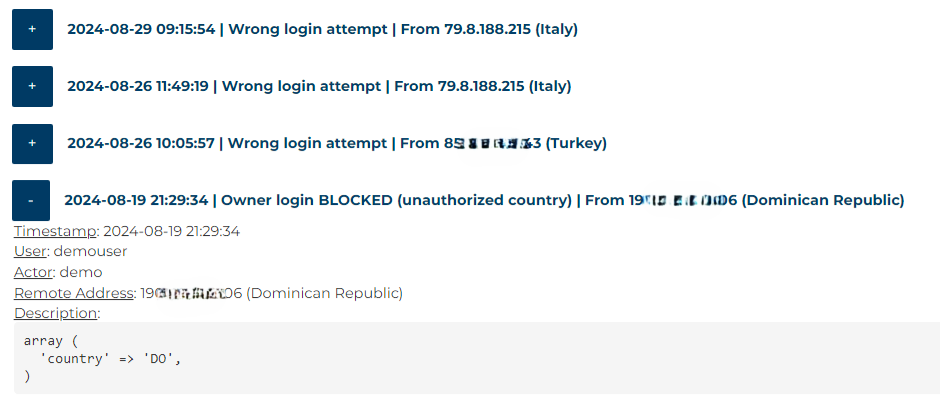
- Customer login BLOCKED (unauthorized country): to authorize nations the tour operator can operate independently in Valid countries for login field from the Security page of the client
- Owner login BLOCKED (unauthorized country): to authorize nations, contact NetStorming Customer Service
- Supplier login BLOCKED (unauthorized country)
- User disabled (too many login attempts)
- User session destroyed
- Wrong login attempt
- Customer Name: you can freely define the agency name (even just the first few letters) and search for it
- Actor Code: it is possible to freely define the Actor code
- User: it is possible to freely define the User
- Description: you can freely define a description
- Remote Address: you can freely define an IP address
- IP Nationality: you can freely choose a specific country where the IP address belongs
Below is an example of the results with the possibility to expand with + in order to see in detail the security logs referring to a specific access attempt: